I recently came across an old, unopened Lenovo Chromebook 10e tablet from when I purchased two during a 99 dollar (each) fire sale maybe four years ago. Nowadays, they are arguably almost junk, sporting an old MediaTek processor running at 4C, 2.0 GHz, but still with a decent quality 10.1 inch screen at a 1920×1200 resolution and running Chrome OS 64-bit. (At some point in the last few years, they updated the OS to be 64-bit, it definitely used to be only 32-bit not that long ago.) This tablet undoubtedly has seen better days and is quite laggy when it comes to running applications. So, this got me thinking: What can this tablet be good for still in this day and age? — Ah, a portable, battery-powered monitor!
Rewind a few months back, I had purchased a USB-C capture card in a similar effort of trying to accomplish a portable monitor, but with my iPad Pro. The capture card shows up as a webcam with an audio input as well and works decently well with the various iPadOS apps like HDMI Monitor from Orion. However, I have found that I don’t want to relegate my iPad to being just a portable monitor and it would be nice if I just had a semi-dedicated device for this portable monitor functionality — in comes this near-junk-status tablet.
My first stop was of course to the Play Store, why build something when you can just buy it (or download it for free)? But, alas, the “premier” capture card app that I found (CapView), was incompatible with my ancient tablet. This led me down the natural rabbit hole of finding an alternative. One option was potentially using the built in Camera app, but without audio playback and a less than optimal screen-layout in the camera app, the experience was abysmal.
So, I embarked on building my own — one that is low resource enough for an old tablet and one that is ideally relatively portable. Knowing that the USB capture card is exposed as a camera and microphone, a few choices came to mind: build a basic Android camera app, which would require me to restart my Android development days; or, I could just build it as a web app utilizing the latest in HTML5 technologies (navigator.mediaDevices.getUserMedia)!
A few short hours of writing HTML and Javascript later, along with some additional polish like adding a basic CSS theme, drawing an SVG icon, and playing with the layout a bit, the resulting SPA artifact was pushed to Cloudflare Pages and Capture Card was born!
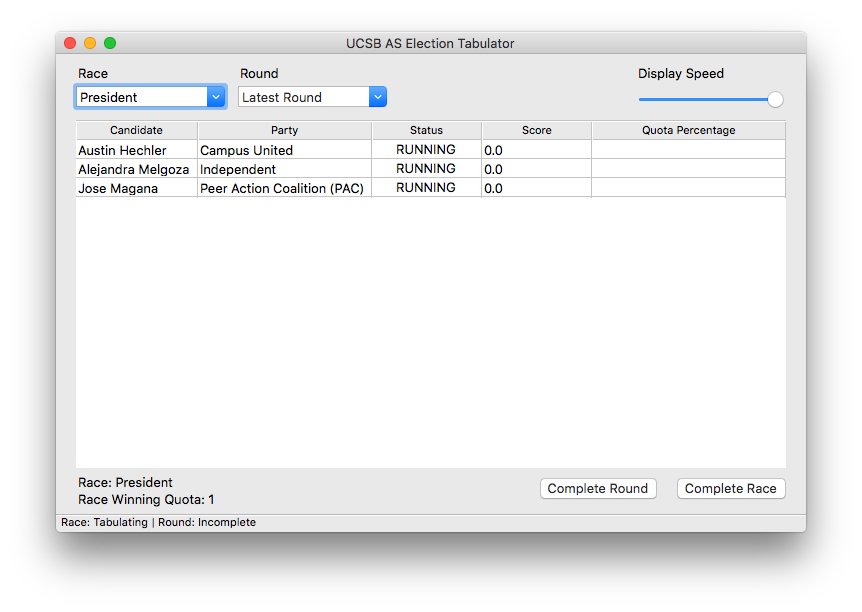
Capture Card is hosted at https://capturecard.pages.dev/, an easy to remember URL that provides a basic page that supports accessing both the camera and microphone of a capture card. It exposes the devices as a basic video element, initially muted in-case you accidentally have an audio loop, and allows you to enable a fullscreen or picture-in-picture experience with the native video element. For added convenience, you can even use the query parameters video and audio to leverage name-based matching for the two devices. For example, https://capturecard.pages.dev/?video=usb&audio=usb will automatically use the devices that contains the word usb inside it, making it super easy to quickly open the right devices from a bookmark.
The entire tool is hosted as a single HTML page, with zero external dependencies, requiring no long term maintenance as the tool doesn’t require updating unless the HTML/Javascript spec changes in some incompatible way. It is quick and easy to use on a Chromebook tablet like the one I have and does the job. Hopefully someone else comes across this tool and finds it useful to their flow. For now, I have found a new purpose for an old tablet.
Got feedback? Leave a comment! I would appreciate any constructive feedback you have, or just let me know you’re using it. Enjoy!